Let’s look into what VPC endpoint is and what it is for.
In typical scenario when connecting to other AWS services in a Virtual Private Cloud in AWS, we obviously need a connection whether it is over an internet or private network through NAT gateway or instance or VPN connection or Direct Connection.
However, VPC endpoint does not need any help from those services to get it work. It guarantees that traffic does not go out of AWS network.
Here the words “Endpoints” are Virtual Devices.
There are two types of VPC Endpoints
- Interface Endpoints
→ This is an elastic network interface with a private ip address from the IP address range of your subnet that serves as an entry point for traffic destined to a supported service. and it’s powered by AWS PrivateLink.
- Amazon API Gateway
- Amazon AppStream 2.0
- AWS App Mesh
- Amazon Athena
- Amazon Cloud Directory
- AWS CloudFormation
- AWS CloudTrail
- Amazon CloudWatch
- Amazon CloudWatch Events
- Amazon CloudWatch Logs
- AWS CodeBuild
- AWS CodeCommit
- AWS CodePipeline
- AWS Config
- AWS DataSync
- Amazon EC2 API
- Amazon Elastic File System
- Elastic Load Balancing
- Amazon Elastic Container Registry
- Amazon Elastic Container Service
- AWS Glue
- AWS Key Management Service
- Amazon Kinesis Data Firehose
- Amazon Kinesis Data Streams
- Amazon Rekognition
- Amazon SageMaker and Amazon SageMaker Runtime
- Amazon SageMaker Notebook
- AWS Secrets Manager
- AWS Security Token Service
- AWS Service Catalog
- Amazon SNS
- Amazon SQS
- AWS Systems Manager
- AWS Storage Gateway
- AWS Transfer for SFTP
- Endpoint services hosted by other AWS accounts
- Supported AWS Marketplace partner services
2. Gateway Endpoints
→ This is a gateway that you specify as a target for a route in your route table for traffic destined to a supported service. and the following services are supported
- Amazon S3
- DynamoDB
What about permissions to VPC endpoints?
IAM Users don’t have permissions to work with VPC endpoints by default, so you need create IAM user policy that grants users the permissions to work on CRUD endpoints. And currently, resource-level permissions are not supported for ec2:*VpcEndpoint* API actions
How to control access to the VPC Endpoint Service?
when you create a VPC endpoint, you can choose a policy depending on your requirement whether you would like to enable it to permit any user or service within the same VPC or to have custom policy for specific case.
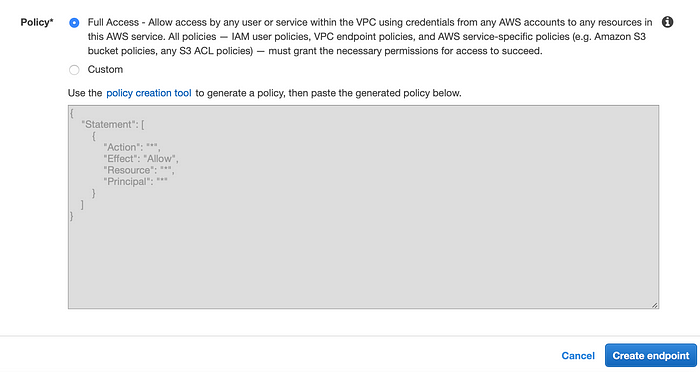
On top of that, as it is specified in AWS Documentation, you don’t attach any policy to VPC endpoint, default policy automatically is attached to it. and the endpoint policy doesn’t override or replace IAM user policy or service-specific policy such as S3 Bucket Policy as it works as separate policy. and anytime you can modify the attached policy with a few minutes to take effect.
VPC Security Group?
When you create an interface endpoints, you can associate security groups with endpoint network interface that is created in your VPC. If you don’t specify any security groups, the default security group will be attached to it. and then you must make sure that rules inside the security group allow traffic the endpoint network interface and the resources in your VPC that connects with the service.

In case of gateway endpoints, if your security group’s outbound rules are restricted, you must add a rule that allows outbound traffic from your VPC to the service that’s specified in your endpoint. To do this, you can use the service’s prefix list ID as the destination in the outbound rule.
